empowering your digital transformation.....we dont negotiate amount for our digital purchase

Empowering, safeguarding your finances and digital assets
Innovative software solutions for a digital-first economy.
Custom Development
Custom Software Development – We design and build tailored applications and enterprise systems that align with your business needs, ensuring scalability, security, and seamless integration.
Cloud Solutions – We deliver scalable SaaS, PaaS, and IaaS platforms with secure cloud migration strategies, optimizing performance and reducing operational costs.
AI & Machine Learning – We create intelligent automation and predictive analytics to turn data into actionable insights.
Scalable Cloud Solutions
Reliable and adaptable technology.
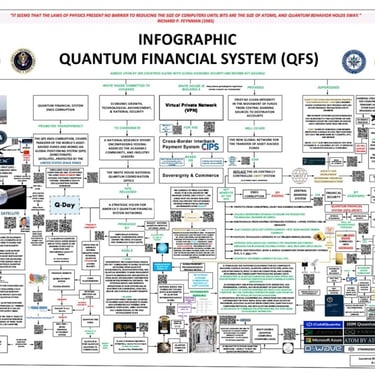
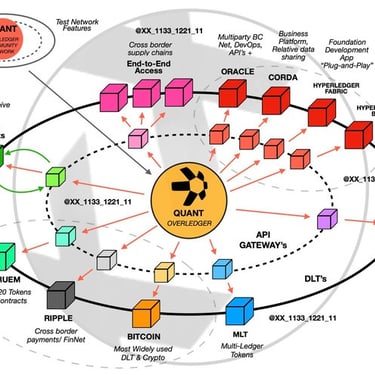
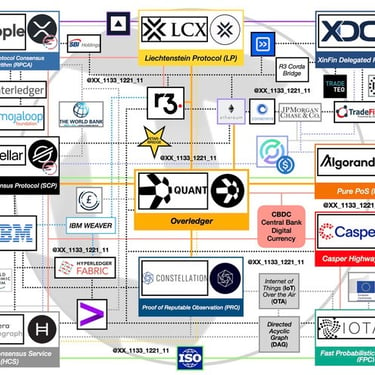
The Quantum Financial ecosystem

Neurasoftdev.com
SECURE YOUR DIGITAL ASSETS & FINANCES USING
THE BIT-QUANTUM DIGITAL LEDGER
Your encrypted gateway to Finances & Digital assets protection
Neurasoftdev.com
price Ranges From $2,500-$5,000



Protecting the Future of Finance Using the Quantum Financial Resistance System
Energy Priorities shift in 2026
What's Driving Energy Decisions in 2026






Clean vs. Reliable Energy Reality


Energy as National security
Neurasoftdev.com






STEVE POPE Jr
Founder of Quantum Computing Investment


Protecting the future of Digital assets
Let's join hands to make the world a better place. Using the Quantum Financial resistance system

About the Quantum-Resistance-system.
The phrase “Quantum Financial Resistance System” (sometimes stylized as Quantum Financial System or QFS) often seems to be the most secure method for financial safety, freedom, and alternative or speculative narratives about global economics, technology, or “secret” financial reforms used to secure & Recover digital Assets for both individuals & companies.


150M+
250k+
Trusted by Leaders
Innovative Solutions
Neurasoftdev.com


Protect Your digital assets & finances
You didn’t come this far to stop


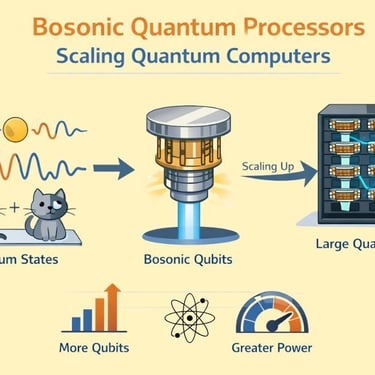
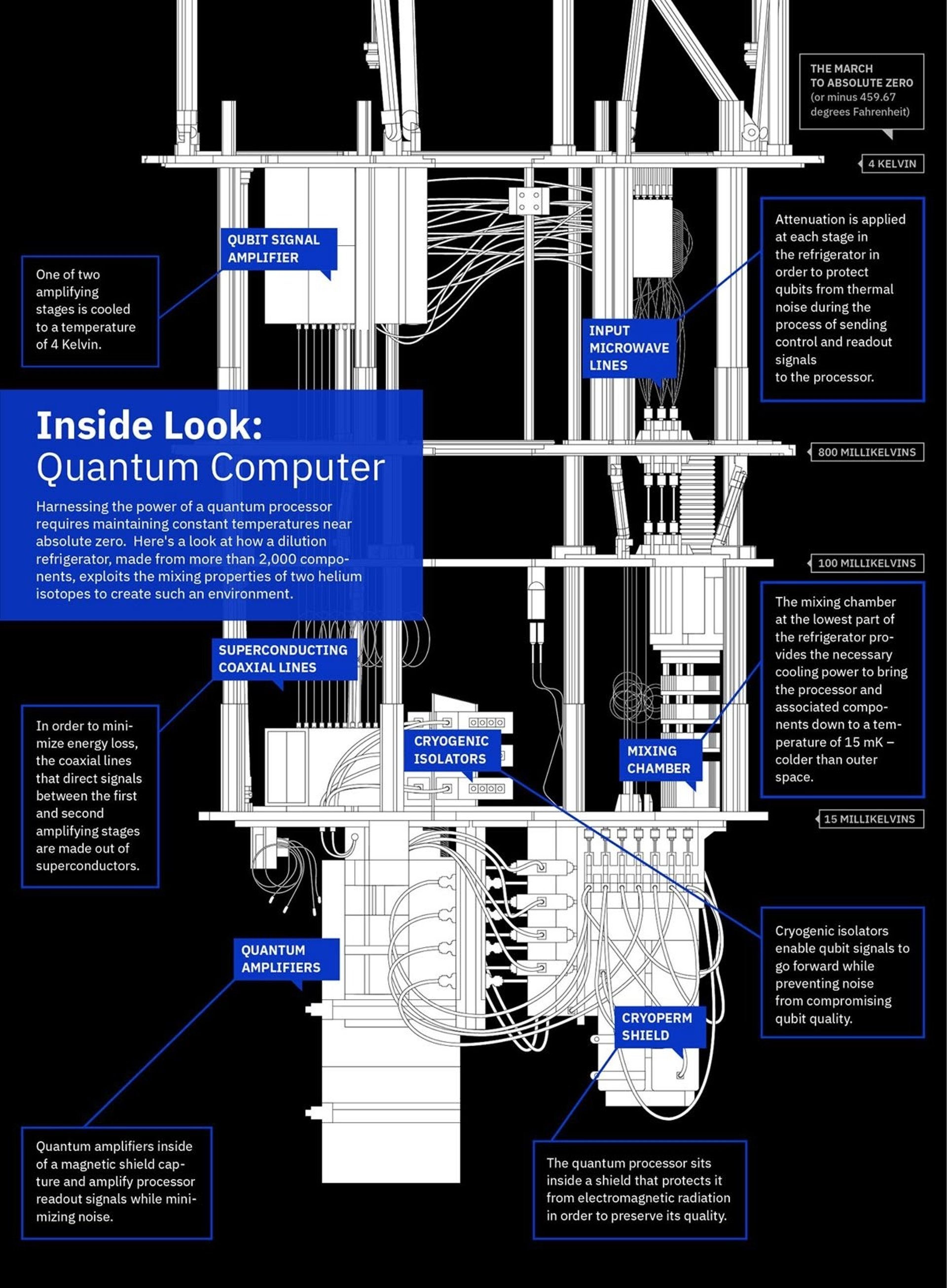
How Quantum Computing works


wifi pernatration software
Marketing blurb (concise):"Wi-Fi Penetration Testing Software a professional toolkit for authorized security assessments that identifies wireless vulnerabilities, validates encryption and configuration, and helps organizations harden their networks."
Technical summary (concise): "An enterprise-grade Wi-Fi penetration platform for authorized auditors that performs controlled vulnerability discovery, protocol and configuration checks, and reporting to prioritize remediation and improve wireless security posture."
Compliance-focused (concise): "A Wi-Fi penetration testing solution designed for use by accredited security teams under explicit authorization — used to safely simulate attacks, document findings, and ensure regulatory and policy compliance."


Identity protection Software
Identity Protection Software: An enterprise-grade security solution that proactively safeguards digital identities by monitoring sensitive information, detecting anomalies, and preventing unauthorized access. Designed to strengthen compliance, reduce fraud risk, and build customer trust, it ensures organizations maintain resilience in today’s data-driven world.


NETWORK PENETRATION TESTING
Network Penetration Testing- A controlled security assessment that simulates real-world cyberattacks to identify vulnerabilities in network infrastructure, helping organizations strengthen defenses, ensure compliance, and reduce risk of breaches.


Protection from malicious App & breaches



Our Partners & certification
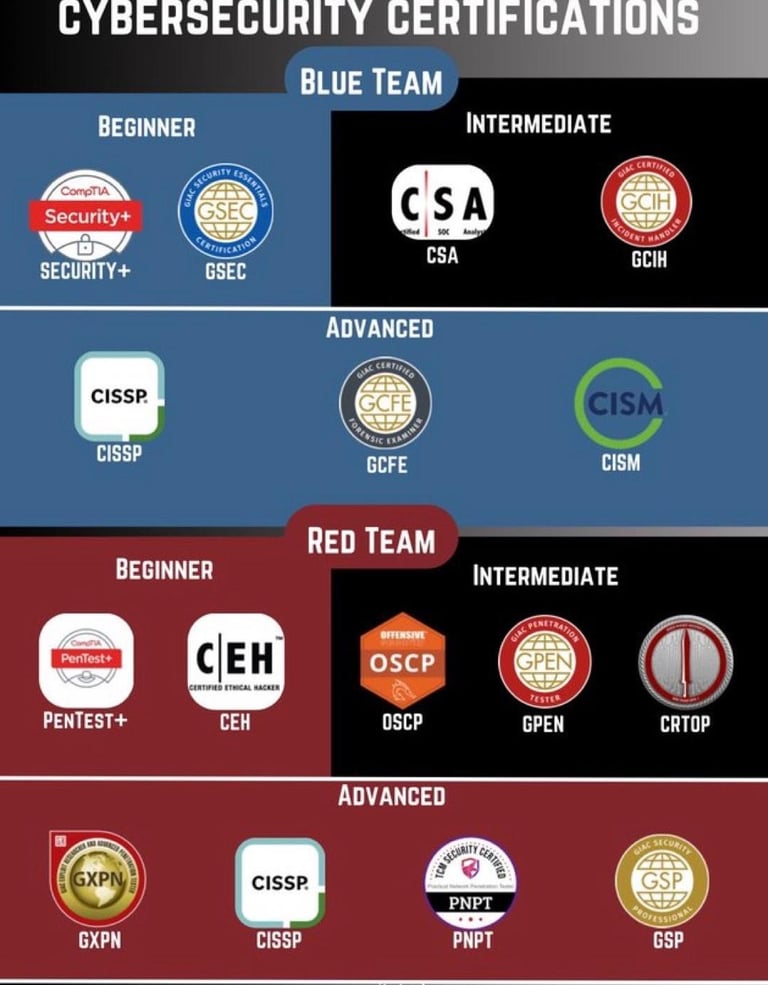
CYBERSECURITY CERTIFICATION


The Antivirus Handbook
HACKER'S HANDBOOK


The Quantum projects
Quantum projects are transitioning from research to tokenization. Governments and corporations view this as a critical technology frontier, shaping defense, finance, logistics, and data security strategies. The guiding philosophy — strategy is not prediction, but precision in motion — perfectly describes how the field evolves: rapid experimentation, adaptive scaling, and iterative progress toward strategic finanxial dominance.


THE QUANTUM STRATEGY
“Strategy is not prediction; it’s precision in motion.”
It sounds like you’re expressing a philosophy about how effective strategy relies on continuous, deliberate action rather than trying to forecast the future. It’s succinct, memorable, and has a strong motivational tone — great for a cover letter or a professional statement.
Would you like me to help you expand that idea into a paragraph or use it as a hook for your cover letter? For example, we could open with something like:
“Strategy is not prediction; it’s precision in motion. I believe that great results come from purposeful action backed by insight — a mindset I bring to every project I lead.”
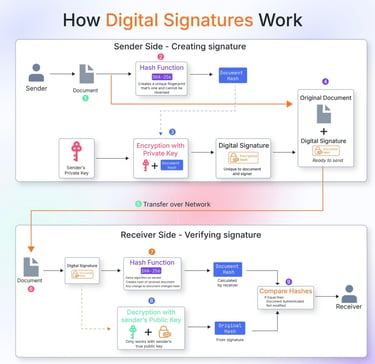
Learn how the Quantum-Financial-Resistance Computing System works.
Dive into the world of Quantum Computing & financial Resistance System and ways of protecting & safeguarding our Financial Assets, including our Digital Assets from malicious Hackers & Fraudsters Globally using The QFS System

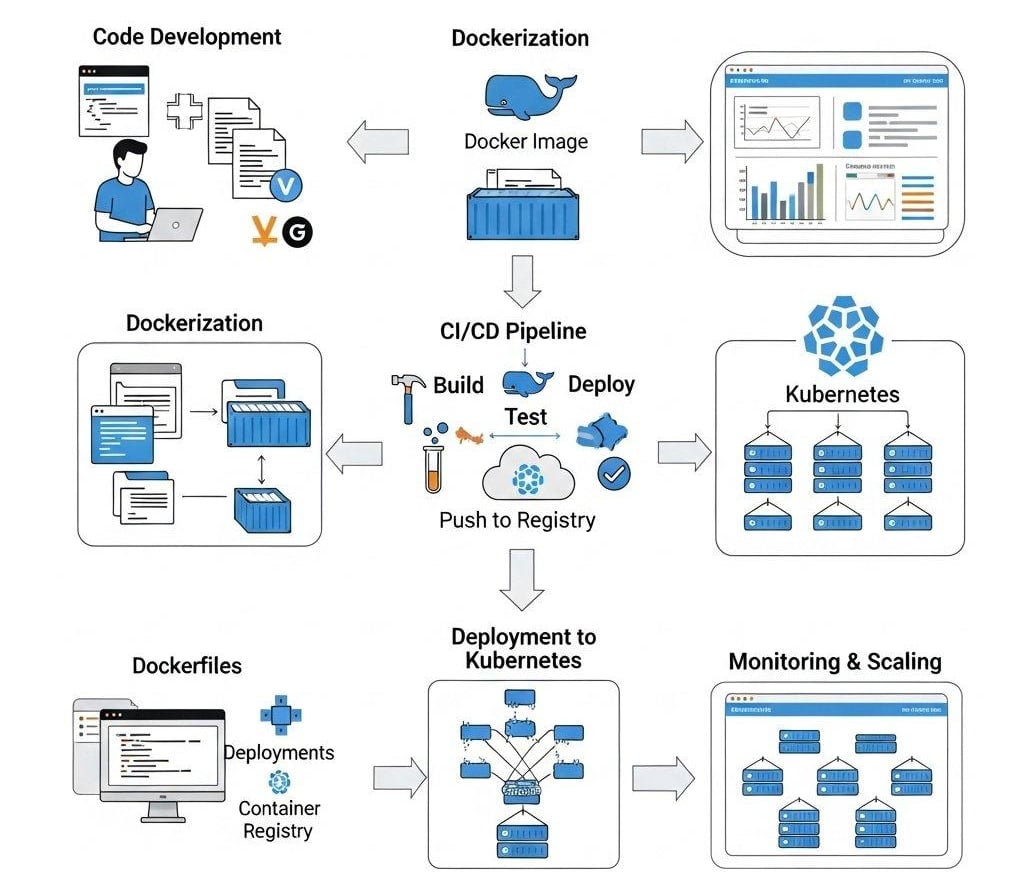
Our Services
Delivering intelligent, scalable, and reliable technology solutions tailored for your business needs.
Custom Development
End-to-end design, development, and deployment of software solutions that drive business success.


Innovative Design
Forward-looking design that enhances user experience and meets real-world challenges effectively.
Empowering organizations with technology solutions that adapt to the digital-first economy.
Scalable Solutions




Stay Connected with Neurasoft
Get the latest updates and insights.