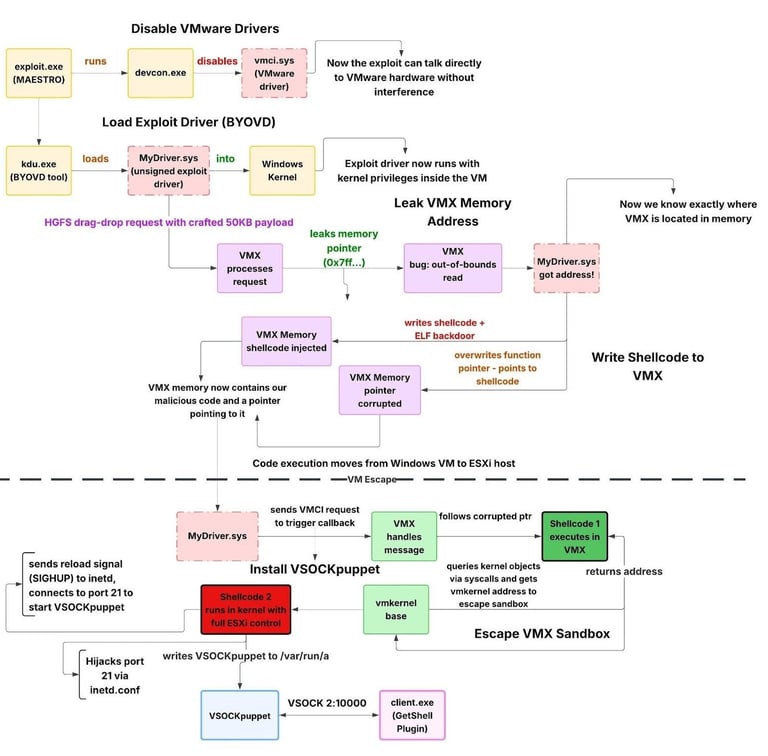
"When VMX handles the message, it follows the corrupted pointer and jumps to the attacker's shellcode instead of legitimate code. This final stage corresponds to CVE-2025-22225, which VMware describes as an 'arbitrary write vulnerability' that allows 'escaping the sandbox.'"
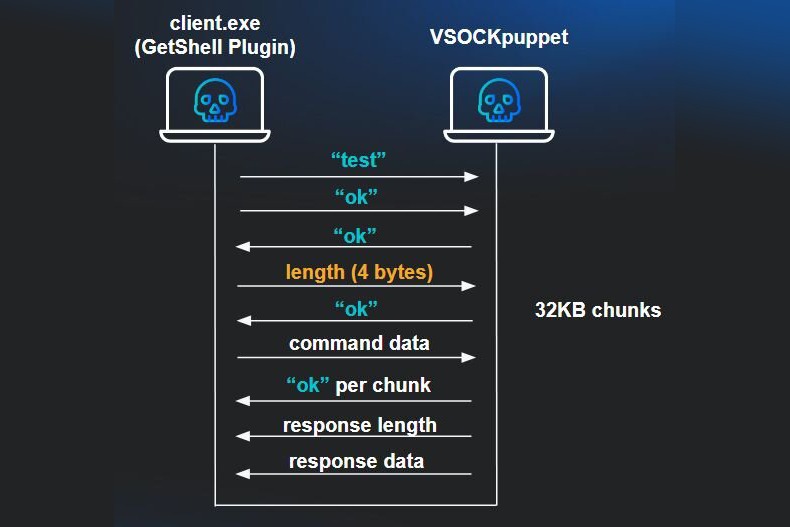
Because VSOCK provides a direct communication channel between guest VMs and the hypervisor, threat actors have been observed using a "client.exe" (aka GetShell Plugin) from any guest Windows VM on the compromised host to send commands back to the compromised ESXi and interact with the backdoor. The PDB path embedded in the binary reveals it may have been developed in November 2023.
The client supports downloading files from ESXi to the VM, uploading files from the VM to ESXi, and executing shell commands on the hypervisor. Interestingly, the GetShell Plugin is deployed to the Windows VM as a ZIP archive ("Binary.zip"), which also includes a README file with usage instructions, providing insight into its file transfer and command execution features.
It's currently unclear who is behind the toolkit. Still, the use of simplified Chinese, coupled with the sophistication of the attack chain and the abuse of zero-day vulnerabilities months before public disclosure, likely points to a well-resourced developer operating in a Chinese-speaking region, Huntress theorized.
"This intrusion demonstrates a sophisticated, multi-stage attack chain designed to escape virtual machine isolation and compromise the underlying ESXi hypervisor," the company added. "By chaining an information leak, memory corruption, and sandbox escape, the threat actor achieved what every VM administrator fears: full control of the hypervisor from within a guest VM."
"The use of VSOCK for backdoor communication is particularly concerning, as it bypasses traditional network monitoring entirely, making detection significantly harder. The toolkit also prioritizes stealth over persistence."
Pham, a senior tactical response analyst at Huntress, told The Hacker News that there is no evidence to suggest that the toolkit was advertised or sold on dark web forums, adding that it was deployed in a targeted manner.
"However, given the presence of a README file with operational instructions, the toolkit was clearly designed for distribution beyond the original developer," Pham said. "We assess with high confidence that the toolkit is being sold privately by a Chinese-speaking developer, likely through private channels or closed groups rather than public underground markets."
"The targeted nature of observed deployments suggests the toolkit may be distributed selectively to vetted buyers rather than broadly commercialized, consistent with higher-end offensive tooling that operators prefer to keep out of widespread propagation to avoid detection signature development."
(The story was updated after publication to include additional commentary from Huntress.)
Found this article interesting? Follow us on Google News, Twitter, and LinkedIn to read more exclusive content we post. It